+33% Increase in Legal A2P Traffic Within 9 Months After Implementing EW SMS Firewall: a Project with a Mozambican Telecom Operator
20 may 2025

An SMS aggregator entered the African market and secured its profitability by protecting the mobile operator’s network from "grey" A2P traffic—and itself from unscrupulous competitors. The key to this success was the implementation of the EW SMS Firewall solution.

Why an Aggregator Needs EW SMS Firewall
Aggregators act as intermediaries for delivering OTT messages between services and MNOs. Their revenue comes from the difference between the cost of receiving SMS from services and the price of terminating traffic through operators. To maximize profits, some unscrupulous aggregators attempt to cut costs by routing A2P traffic through "grey" channels.
To reduce termination costs for A2P traffic, some aggregators:
- Disguise commercial messages as subscriber messages by sending them through SIM boxes
- Mask international traffic as local
These "grey" SMS delivery schemes allow dishonest aggregators to artificially lower service rates to platforms like WhatsApp or Google, creating the illusion of cost savings. By undercutting prices, they secure more contracts, making it difficult for those following the rules to compete.
To prevent revenue losses and stay competitive, our client, an SMS aggregator, decided to protect itself from illegal commercial traffic. For this, it chose our solution—EW SMS Firewall. In this project, the firewall needed to be deployed on the side of a Mozambican mobile operator that partnered with our client.
EW SMS Firewall analyzes message delivery routes and blocks "grey" A2P traffic sent to the mobile operator by unscrupulous competitors. Once these messages are blocked, OTT services that initially used these aggregators must resend their SMS. This time, they usually opt for legitimate routes provided by our partner to ensure successful delivery. As a result dishonest competitors lose their termination contracts and our client has a better chance of securing new deals.
Apache Kafka and Other Challenges for the Eastwind Team
Typically, telecom operators use the SS7 signaling protocol or a direct SMPP connection with an aggregator to deliver international A2P SMS. However, in this case, the African operator transmits messages through its own API, built on the Apache Kafka message broker. Not all vendors are willing to adapt their solutions to non-standard architectures, as it requires significant investment.
Despite the need for modifications, the Eastwind team took on the project. It was an opportunity not only to deepen their expertise in traffic monitoring but also to develop a ready-made solution for similar cases in the future.

What We Procured for the Project
At the partner's request, Eastwind specialists assessed the client's system load, selected the necessary hardware from a supplier and prepared it for deployment, providing remote support to the client's team.
Hardware for the Project:
- three servers
- SSD storage shelf
- two switches
- network cables
- additional components
Additionally, Eastwind experts assisted the partner in selecting licenses for the Hyper-V and VCenter virtualization environments. This allowed them to deploy virtual machines on physical servers for Apache Kafka, EW SMS Firewall, Zabbix Proxy, and databases.
What We Upgraded in the System
To enable EW SMS Firewall to process messages using the new method, we made several improvements before integrating it with Apache Kafka. These included:
- adding an Apache Kafka queue service for message processing;
- designing and developing a proxy node to handle request and response transmission between the mobile operator and the EW SMS Firewall core;
- optimizing SMS processing logic by moving some verification checks from external systems into the core, ensuring faster message handling;
- enhancing the web interface for improved usability.
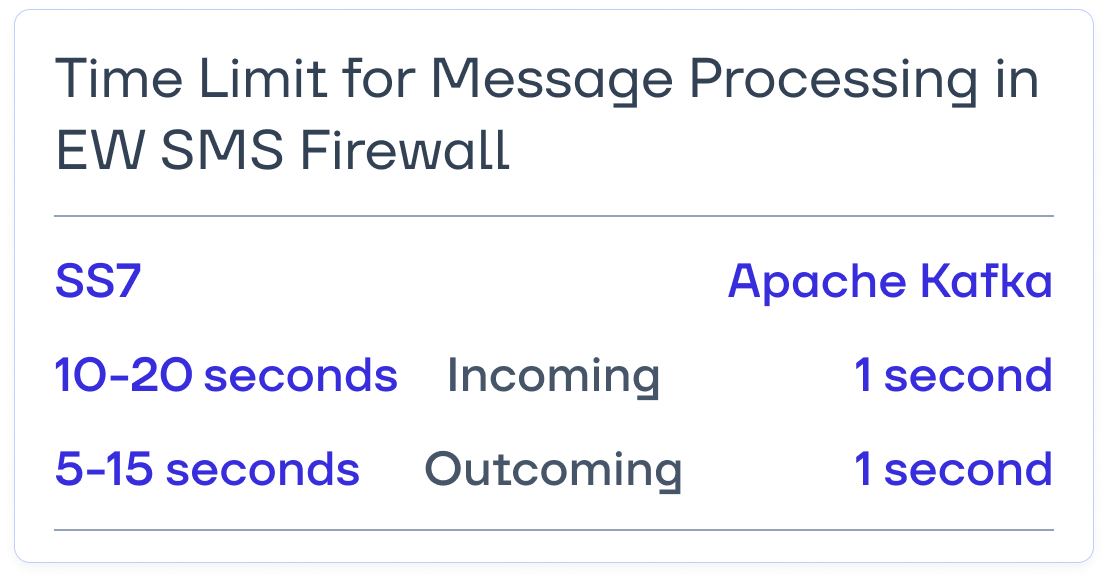
The Apache Kafka message broker imposed additional constraints on message processing, requiring us to modify the architecture of EW SMS Firewall. These changes ensured seamless integration while maintaining efficiency and performance
Implementation Stages
| Stage | Actions Taken | Duration | Outcome | |
| Project Planning | - Held a kickoff meeting; - Developed and approved the project plan with the client. |
4 days | Project plan developed | |
| Preparation for Deployment | Developed and approved: - High-Level Design (HLD) - Low-Level Design (LLD). |
6 days | HLD and LLD completed | |
| Hardware Setup | - Client configured remote access; - Prepared hardware for software installation; - Installed EW SMS Firewall. |
12 days | EW SMS Firewall installed on client servers | |
| Integration with Operator Network & System Configuration | - Integrated EW SMS Firewall with Apache Kafka; - Tested EW SMS Firewall; - Performed system configuration; - Approved the acceptance checklist. |
15 days | EW SMS Firewall successfully integrated with Apache Kafka | |
| Acceptance Testing | - Conducted acceptance testing; - Signed the acceptance report with the client. |
4 days | Acceptance report signed | |
| Commercial Deployment | - Performed live traffic migration; - Verified system performance; - Conducted final validation. |
7 days | EW SMS Firewall successfully deployed into commercial operation |
How We Refined the System Logic
Clients accept implementation projects based on a checklist that verifies system performance under conditions close to real-world usage. For example, during EW SMS Firewall testing, the operator sends predefined fraudulent SMS messages, which the platform must successfully block.
While testing EW SMS Firewall in Mozambique, we identified an issue: The filter was malfunctioning, and the platform was not blocking all fraudulent SMS messages as intended. The root cause was traced back to the migration of validation processes into the system’s core, which disrupted the request processing logic. We rectified all the shortcomings within a week, and during the second round of testing, EW SMS Firewall successfully passed all the checks.
“We essentially developed a new version of the product to operate across the channels it had never used before. Implementing such extensive modifications within the extremely tight deadlines set by the client was a challenging task. But we succeeded and launched on time.”
Andrey Simonov,
Head of Mobile Messaging Group, Eastwind Computer Telephony Department
Head of Mobile Messaging Group, Eastwind Computer Telephony Department
What About Client's KPI Performance?
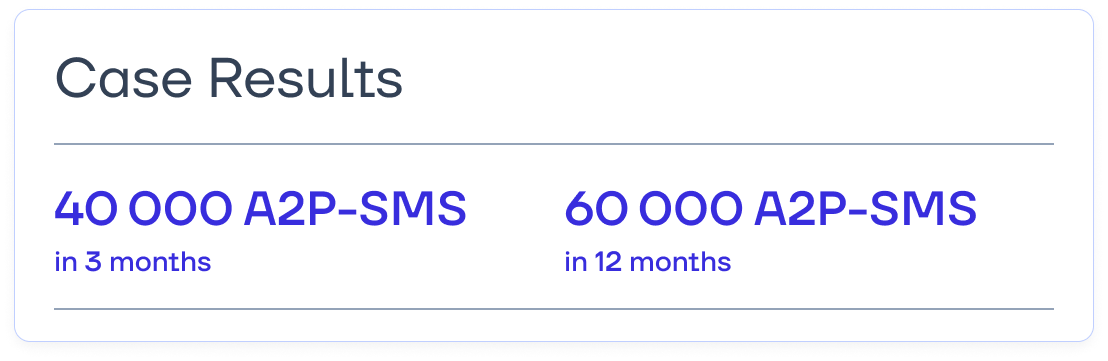
To reach the expected revenue from A2P traffic monetization as quickly as possible, the client not only deployed the EW SMS Firewall platform but also signed a Managed Services contract. This collaboration model ensures full support for EW SMS Firewall with Eastwind specialists continuously monitoring newly emerging fraud schemes and updating filters. This proactive approach is crucial, as fraudulent aggregators constantly develop new ways to bypass message delivery restrictions. Keeping filters updated is key to maintaining optimal performance. Additionally, our partner set a KPI of 40,000 international A2P SMS per day to secure the necessary revenue level.
3 months after the project completion, the client successfully met its traffic volume target—40 000 SMS per day. Today, the results exceed expectations. The client is now handling 60 000 legitimate A2P messages daily, generating even higher revenue than originally planned.
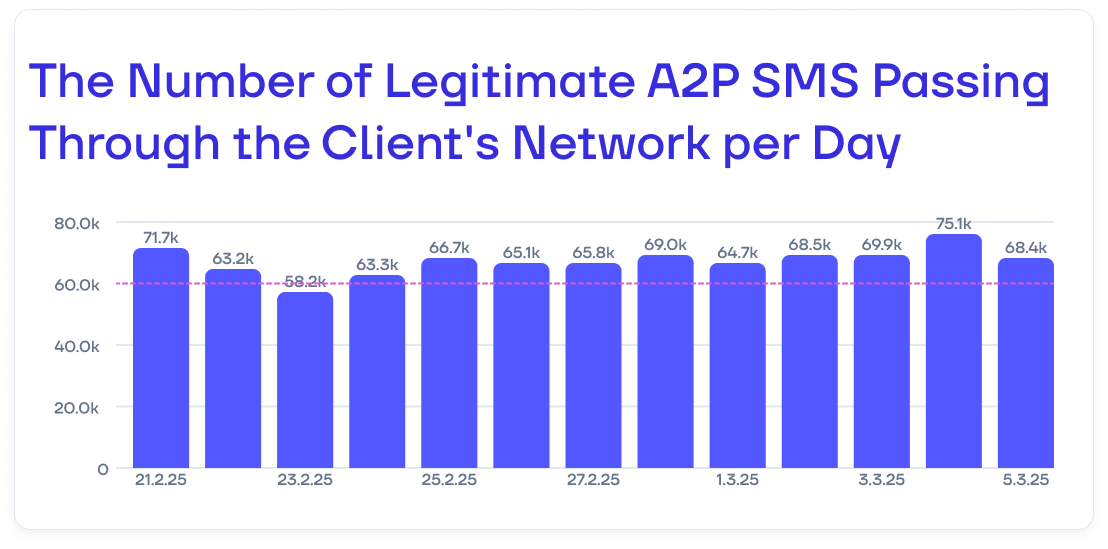
Fraudulent content providers constantly develop new methods to bypass EW SMS Firewall filters. However, thanks to continuous monitoring and proactive filter updates, we consistently maintain performance above the target KPI
Follow-Up Operations After Implementation
The client collaborates with Eastwind under the Managed Services model, meaning our specialists handle ongoing monitoring and optimization. We continuously track new fraudulent schemes and adjust filters accordingly. The client receives daily reports via email. At any time the client can access built-in dashboards for live monitoring and insights.
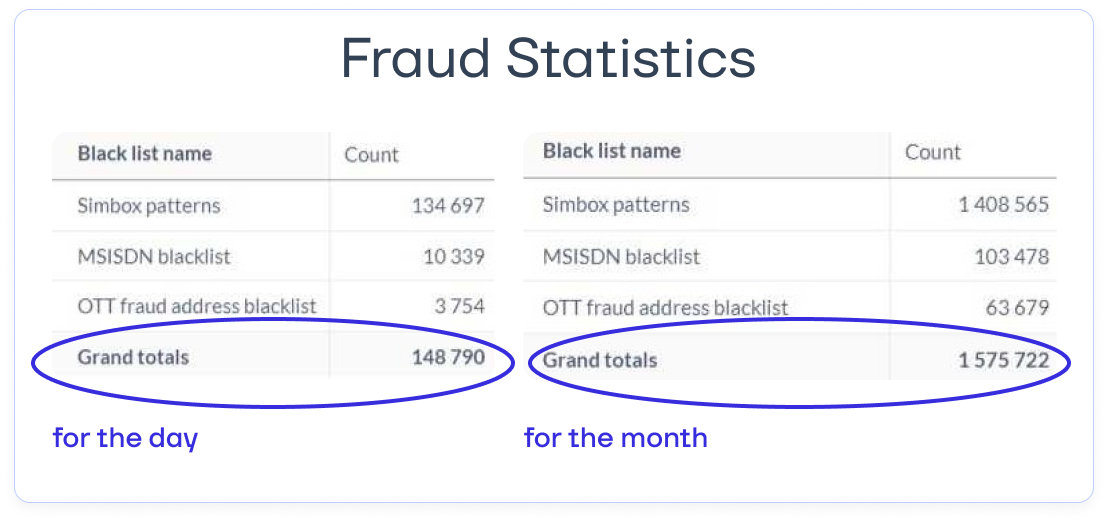
EW SMS Firewall logs and analyzes various fraud attempts, including: SIM box exploitation, MSISDN or sender name spoofing
"Fraudsters and unfair SMS aggregators constantly invent new ways to bypass anti-fraud systems. That’s why we monitor metrics non-stop and promptly update settings to prevent revenue loss for the operator and ensure expected profitability."
Irina Timofeeva,
Eastwind Customer Success Manager
Eastwind Customer Success Manager
Learn more about the EW SMS Firewall
